7 big questions answered on 3rd party penetration testing

If I asked you how secure your company's network is right now, how would you respond?
Most business owners might say that their systems are quite secure, even when facing strict regulatory compliance. After all, they have all the security controls in place and their IT teams are continuously testing their efficiency.
Let’s look at the facts, then we'll explore where 3rd-party penetration testing comes into play.
How vulnerable to breaches are companies today?
Ultimately, recent reports and public breaches have shown us that more must be done on a regular basis to further safeguard companies from potential cyber attacks. In fact, according to information security company Trustwave:
 Source: 2019 Trustwave Global Security Report
Source: 2019 Trustwave Global Security Report
That same report indicated that the median number of vulnerabilities detected per application was 15.
So allow me to ask that question again: how secure is your network, really?
Many companies worldwide have suffered a data breach or cyber attack when they least expected it, causing great financial damages and starting further investigations into their security procedures.
Here’s a bit of good news, though:
The median time between intrusion and detection for externally detected compromises was 55 days in 2018, down from 83 days in 2017. This is the period of time that allows attackers to obtain sensitive data from a company’s systems and set up mechanisms to collect and extract new data as it’s added.
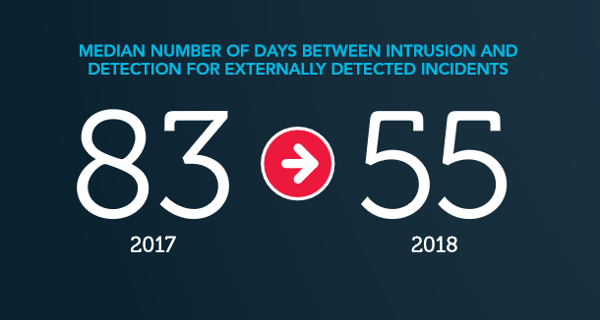 Source: 2019 Trustwave Global Security Report
Source: 2019 Trustwave Global Security Report
Though we might be getting slightly faster at detecting breaches, third-party organizations are still leading the way in detection versus victim organizations themselves.
“Victim organizations detected fewer than half of data breaches in 2018, with third-parties, regulatory bodies, or attackers themselves detecting the rest.” - Trustwave Global Security Report, 2019
Thwart cyber attacks with third-party penetration testing
So we’re aware that data breaches and compromises are happening at an alarming rate. But how do companies actually get better at combating them?
Apart from having in-house teams to test the security of their systems, organizations should use regular third-party penetration testing for their cybersecurity risk assessment.
Penetration testing, also called pen testing, is a real-world attack simulation launched on a computer system to uncover vulnerabilities and test the efficacy of a company’s information security program. It's also referred to as ethical hacking as it includes consent between the business and the tester and is performed in a controlled environment.
To clear up confusion you might have around this technical process, I'll answer 7 major questions around penetration testing and why it's essential for your business.
1. Why is penetration testing important for securing your organization?
2. Where does your visitor management system come into play?
3. How often should you perform penetration tests?
4. What are the main types of penetration tests?
5. What are the main benefits of penetration testing?
6. Is penetration testing dangerous for your network?
7. What are some final things to remember about third-party penetration testing?
1. Why is penetration testing important for securing your organization?
First things first, the main objectives of penetration tests are to:
- Identify potential breach sites and vulnerabilities through in-depth analysis
- Simulate cyber attacks by penetrating vulnerable systems and applications using both manual and automated tools
- Gain access to sensitive data and/or systems
As modern IT environments are becoming more and more complex, a company’s IT team can get overwhelmed by potential vulnerabilities that could affect the respective network.
Penetration testing serves as a valuable tool that allows for validation and prioritization of vulnerabilities. This provides IT teams with the opportunity to solve those vulnerabilities that hackers can easily and quickly exploit, particularly that could do the most harm.
2. Where does your visitor management system come into play?
An addition to physically securing your premises, a cloud-based visitor management system (VMS) like Proxyclick has the important responsibility of keeping your data secure. After all, we capture the sensitive information of millions of guests at organizations around the world. (By the way, find out if your company should complete the Cloud Security Alliance CAIQ here).
To protect your networks, your business, and your people, performing third-party penetration tests is extremely important from a VMS providers' standpoint.
At Proxyclick, our team performs these penetration tests using select third-party clients on an ad hoc basis, in addition to our extensive internal scanning and testing program. We also employ third-party security experts annually to perform a broad penetration test across the Proxyclick service offering. (By the way, check out our
3. How often should you perform penetration tests?
Generally, security specialists recommend having a penetration test annually, or whenever a large network change has occurred.
4. What are the main types of penetration testing?
There are two main types of penetration tests: black box and white box tests.
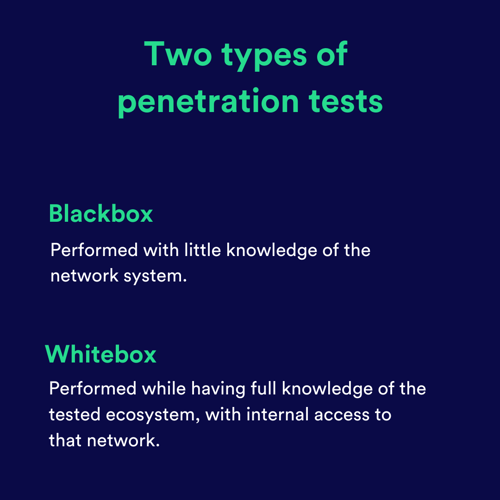
Let's break down the differences:
- Black box tests: these are performed with little knowledge of the tested network ecosystem - mostly what is already publicly available on the Internet. A black box test is essentially an objective assessment of a company’s security as seen from an external attacker’s perspective.
- White box tests: These are performed while having full knowledge of the tested ecosystem and even internal access to that network. A white box test highlights the great threat posed by insiders who are given physical and logical access to IT resources by a company.
Selecting the right approach to penetration testing is essential for obtaining relevant results regarding the company’s security risk.
Keep in mind: a white box test can uncover where a developer accidentally left credentials in the software code, but it will be inadequate in uncovering vulnerabilities in open ports or third-party integrations.
5. What are the main benefits of penetration testing?
There are a number of benefits pen tests can bring to your organization. Here are a few of the main ones:
- Avoiding financial damage caused by a security breach
- Managing risk more effectively
- Having a clearer perspective over your security procedures
- Preventing client-side cyber attacks
- Assessing response time to security threats
- Improving existing security status
- Complying with security regulations
- Protecting clients’ sensitive data efficiently
- Protecting your reputation and your products/services
6. Is penetration testing dangerous for your network?
The answer to this question comes down to choosing the right provider, as we have done here at Proxyclick. Professional penetration testing teams will have multiple safety measures in place to limit any impacts on your network.
A good service provider will:
- Ensure that you are both on the same page when it comes to the objective of the test and that there is a realistic scope written down in a formal proposal.
- Respect a clear schedule for when tests will be performed so that any interruption of existing services is avoided.
- Sign and respect a non-disclosure agreement (NDA) which protects the privacy of the company’s sensitive data.
- Have a well-documented testing methodology and they share it with you - this documentation should follow the standards of the Open Source Security Testing Methodology (OSSTMM).
- Report all findings with complete honesty and transparency and offer non-technical and actionable recommendations that can be easily understood by management and staff.
7. What are some final things to remember about third-party penetration testing?
Penetration tests can also be customized to search for vulnerabilities in web applications, mobile devices, wireless networks, and physical security controls.
And while a pen test involves the use of automated tools and process frameworks, the focus is actually on the team of testers, the experience they bring to the test, and how they leverage their skills and resources when simulating the attacks.
This is actually the most essential aspect of pen testing.
Even the most advanced networks are often vulnerable to the singularity of the human mind, which is able to think laterally and outside the box and is equipped with motive and determination when breaching a system.
Ready to talk about how Proxyclick can help secure your organization with third-party penetration tests and more? Try Proxyclick free or book a demo now.


