The regulatory compliance guide for visitor management
For companies who mean to keep their data security risks under control for successful corporate governance
For companies who mean to keep their data security risks under control for successful corporate governance
With the ongoing wave of data privacy reformation taking place across the globe, with no real end in sight, the general cost of data protection compliance is expected to double over the next five years. Double!
But that’s nothing compared to the costs of non-compliance. If your organization aspires to comply with all the global laws, policies, and regulations around your visitor management, then we've got you covered.
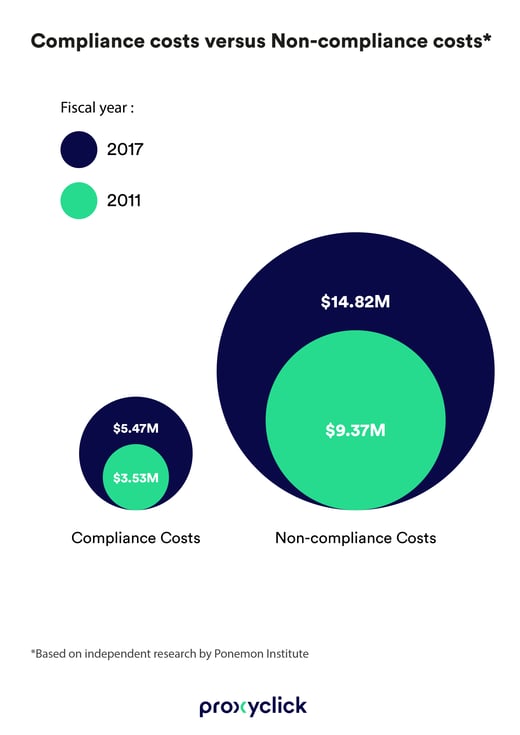
In 2017, an independent study by the Ponemon Institute, commissioned by Globalscape, determined a spike of nearly 45% in costs relating to non-compliance since 2011. This, after interviewing 237 individuals involved in compliance activities in 53 global organizations.
The final tally?
An average of $14.82 million in penalties in 2017—and this was way before the GDPR ever hit.
Incidentally, "compliance activities" can be broken down into 3 categories:
Both the risks and rewards associated with regulatory compliance have reached new heights in the sink-or-swim era of data privacy and accountability.
But drowning in potentially crippling costs is no way to go. Your lifeline comes from keeping your customers satisfied and feeling confident that you'll keep them safe.

If you're anything like Proxyclick and want to swim your way to compliance gold, then you've come to the right place. Because, let's face it, there's no one going around handing out "We are compliant" badges. It simply comes down to what your company's DNA is made of.
You'd actually be surprised how much your visitor management system—assuming you have one in place—can help you manage your compliance objectives.
That's why we've created this guide to help explain some of the key global regulations your business must comply with—and how it relates directly to the way you manage your external visitors and contractors.
Here's what we'll cover:
General Data Protection Regulation
GDPR stands for the General Data Protection Regulation, and it went into effect on May 25th, 2018.
Fact: Visitors on the premises of physical businesses are also covered under the GDPR’s scope, so don't fall for the myths about GDPR and visitor management.
This law encompasses the entirety of the European Union (EU) and the countless companies that do business inside its borders as well as those who collect personal data from EU citizens.
It’s also the reason why we find ourselves ticking countless boxes on websites asking us for permission to collect our data.
It's essential for businesses to maintain regulatory compliance with GDPR laws—or else they risk hefty fines for the crime of negligent data security practices.
Fact: Visitors on the premises of physical businesses are also covered under the GDPR’s scope, so don't fall for the myths about GDPR and visitor management.
Meaning, your visitor sign-in sheet is not exempt from GDPR governance. So, if your company has a paper logbook at its front desk that requires your visitors to sign in and out, this too is subject to GDPR compliance.
The GDPR puts in place general principles that have to be respected when processing personal data. These are:
GDPR applies to any processing of personal data, meaning, any data that can be linked to an individual. This includes names, email addresses, car registration numbers, or pictures, therefore, GDPR has fundamental implications for how your visitor data is collected and managed.
So wouldn't it be easier to rely on a cloud-based visitor management system to do all the heavy lifting so you can focus on the welcome?
Chronologically, the Visitor Management System (or the logbook) will be the first thing the auditor will see. We heard from clients' stories about auditors who started their day by playing with the front desk iPad for one hour and seeing it from a data privacy perspective.
Geoffroy De Cooman
Head of Product, Proxyclick
California Consumer Protection Act
CCPA stands for the California Consumer Protection Act, and this regulation is going to go into effect on January 1st, 2020.
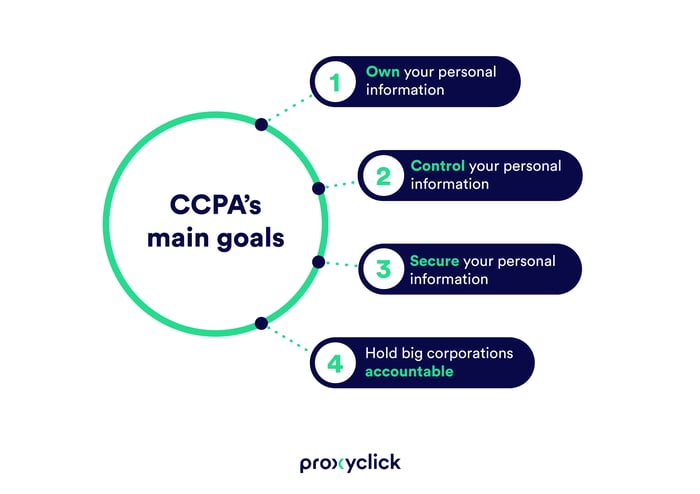
So what is CCPA? It's an act designed to give consumers greater control over their personal data, and the right to know which businesses are using it. (Learn the differences between GDPR and CCPA here).
There are 4 primary goals to the act that you, as a consumer and patron, can be afforded to:
If you're a business owner, this act will require you to disclose specific information you have about your customers and/or visitors (if requested from you).
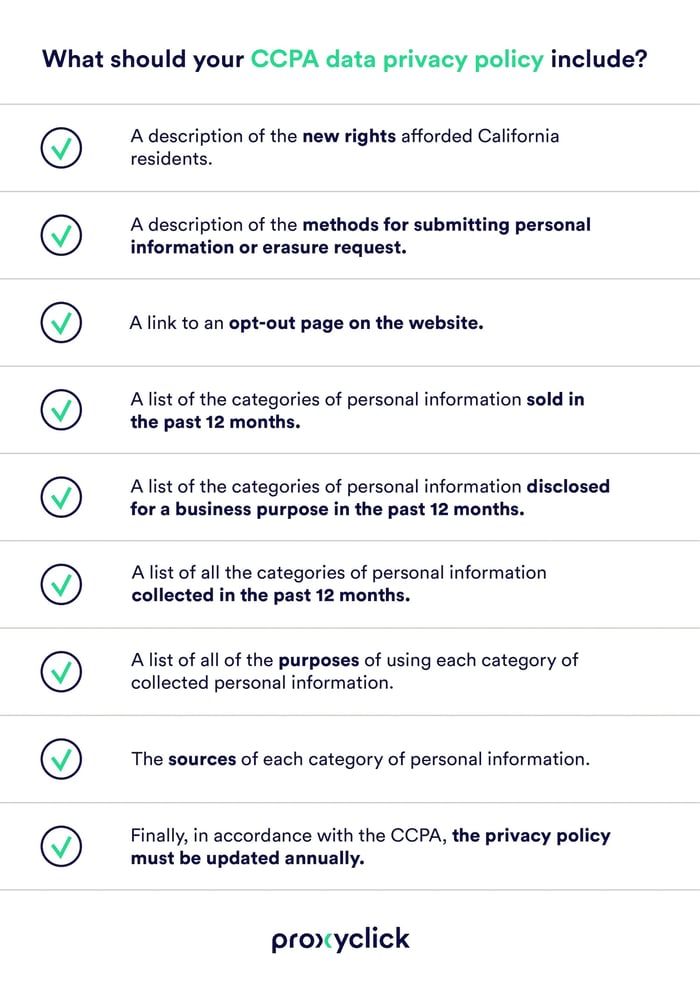
The good news is that this can easily be produced by putting a Data Privacy Policy (DPP) in place with a number of items:
Finally, in accordance with the CCPA, your DPP must be updated annually.
Furthermore, since consumers will also be able to opt out of having their information sold by a company under the CCPA, it could create substantial market changes for businesses that profit from selling customer data.
This includes the information collected from your visitors and external contractors.
Act on the Protection of Personal Information
APPI stands for the Act on the Protection of Personal Information.
Its purpose: To protect the rights and interests of individuals while ensuring due consideration for the usefulness of personal information by basic principles for the proper handling of personal information.
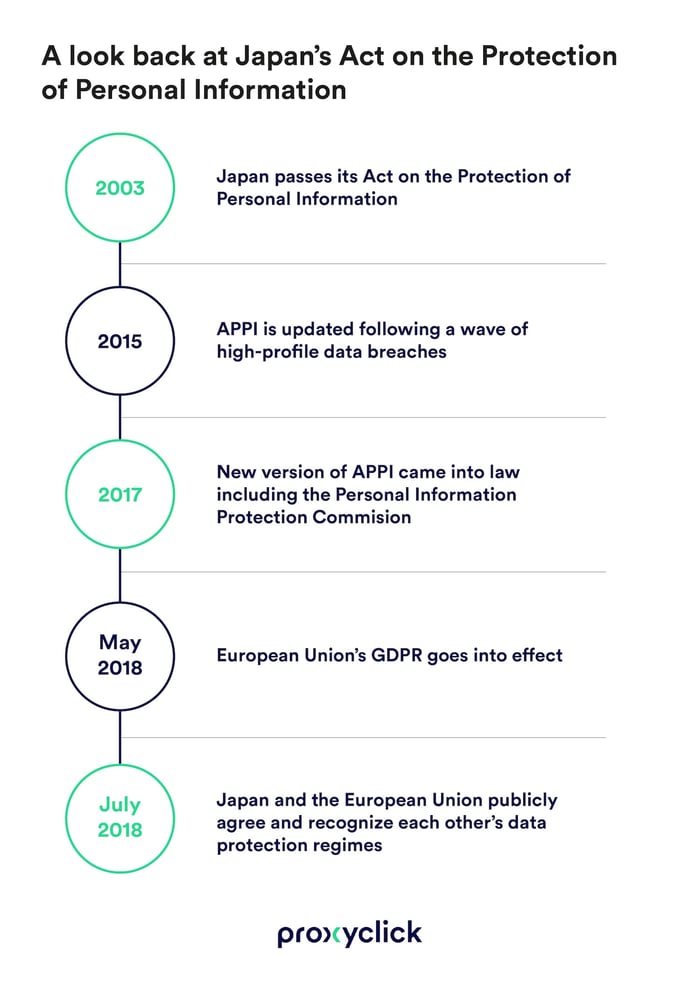
And what most of us don't realize is that it was Japan’s first data protection law that became official in 2003—a whole 15 years prior to GDPR going live.
However, updates were made to this law in 2015 after a wave of high-profile data breaches rocked the country. Back then, over 12.6 million separate data breaches were reported, with roughly 1-in-10 of the nation’s people affected.
The new version of APPI came into law in 2017. With it, the PPC, or, the Personal Information Protection Commission was also brought into effect. If your company handles the personal data of individuals in Japan, then it must comply with these regulation sets.
Then on July 17, 2018, less than two months after the EU's General Data Protection Regulation (GDPR) went into effect, Japan and the European Union publicly agreed and recognized each other’s data protection regimes (despite some natural variations to their regulations).
They stated that that both laws "provided adequate protections for personal data."
Cheers to that!
Under the APPI people can also request businesses to disclose the data that has been collected from them, access that specific information, and demand that the company suspend their data collection efforts on them if desired.
Notably, Japanese consumers now also have the right to sue companies that fail to answer APPI-related questions within two weeks. In addition to the costs of being sued, Japanese business owners can face fines of up to 500,000 Japanese yen and a year of jail time for failure to comply with the APPI.
Payment Card Industry Data Security Standard
PCI DSS stands for the Payment Card Industry Data Security Standard, which includes regulations and rules that are aimed at protecting consumers data in regards to their credit cards, debit cards, and cash cards.
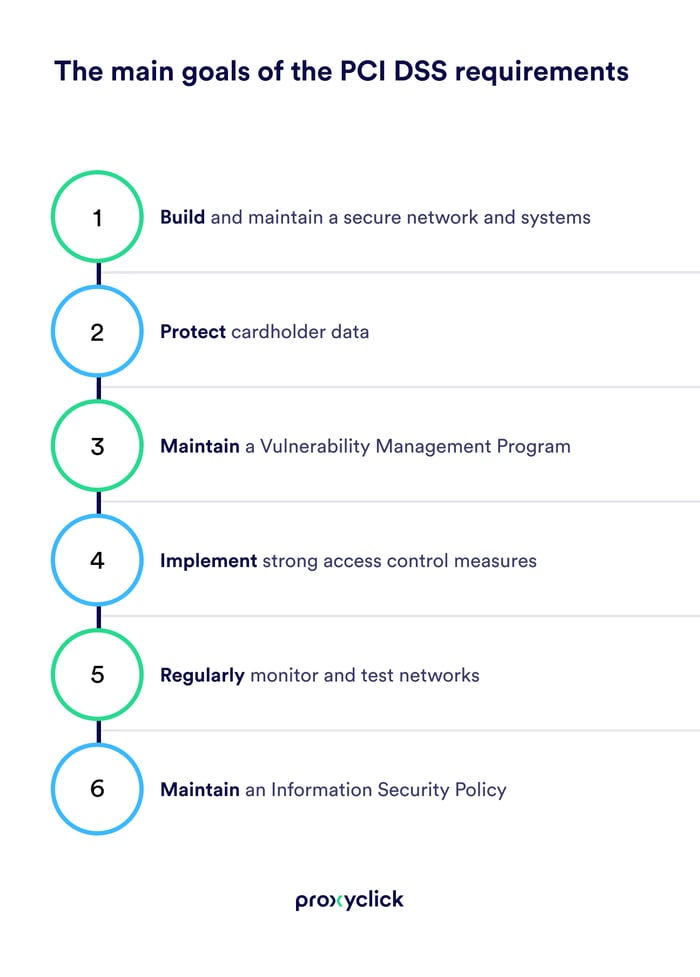
The main goals of the PCI DSS requirements are very straightforward:
PCI DSS applies to any organization with a merchant ID that either transmits or processes information related to credit card holder data.
There are twelve major requirements for PCI DSS compliance:
In 2014, Home Depot was hacked, resulting in the information from 56 million credit cards and debit cards being stolen. To compensate for the damages, the company ended up paying out a total of $159.5 million to date, and that was five years ago.
The consequences for such a violation occurring today have since grown more severe. And it's not just malware or hacks that you need to be wary of. Your company's also got to secure specific ares of your business where this data might be stored.
International Traffic in Arms Regulations
ITAR stands for the International Traffic in Arms Regulations, and it specifically addresses any companies involved with the U.S. defense industry.
The regulations primarily relate to the export and import of defense-related services, articles, and technologies defined under the U.S. munitions list.
If your company does business, of any kind, with the United States military, it must be compliant with ITAR. So even if you only deal with information related to items on the U.S. munitions list, then you're still required to comply with its rules.
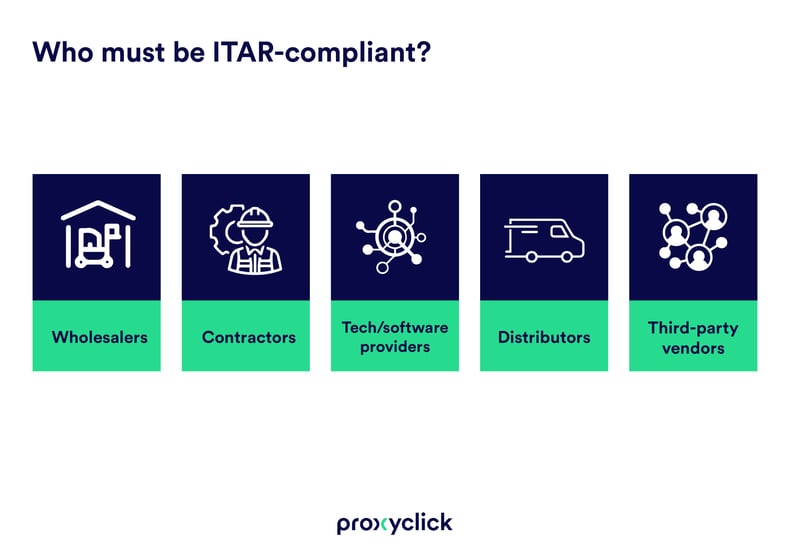
This could mean you fall into any of five categories:
In case you're wondering what constitutes U.S. munitions falling under ITAR's jurisdiction:
The penalties for violating ITAR rules are extremely strict. Civil fines can span up to $500,000 per violation, with criminal charges reaching $1,000,000 and potentially including 10 years jail time.
There is zero room for error when it comes to maintaining ITAR regulatory compliance. It's your responsibility to make sure that sensitive information isn't accessible to just anyone.
For this reason, your company needs to also take extreme care of your external visitors and contractors. Access control technology that's integrated with your visitor management system becomes a must-have, not only for security but for financial savings in cutting the need for personal escorts.
Customs-Trade Partnerships Against Terrorism
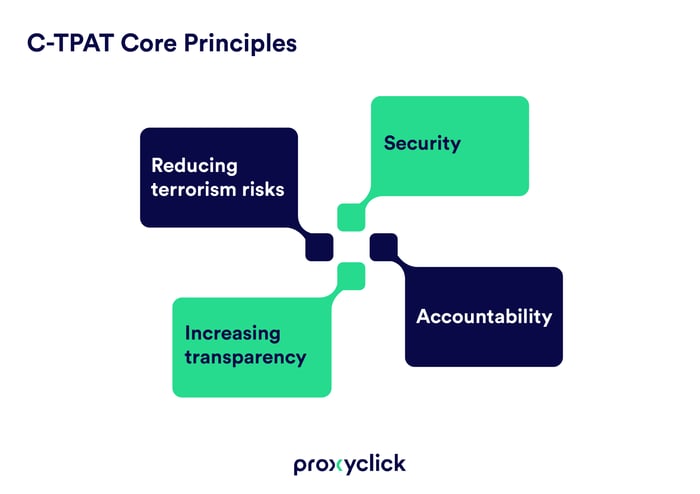
C-TPAT stands for the Customs-Trade Partnership Against Terrorism, and was developed for two major purposes:
The C-TPAT was launched in 2001, and is a voluntary joint-government partnership. Over 10,000 companies are C-TPAT-certified, with roughly 50 percent of them being importers.
If your company wants to achieve a C-TPAT certification, you have to have a documented process for determining and reducing risk throughout their international supply chain.
There many benefits to being C-TPAT-certified. To name a few:
Only certain types of companies can be accepted into C-TPAT, and they must meet a range of specific and unique requirements.
They are, though, focused around four core principles:
Here is a list of company types that are eligible to apply for C-TPAT certifications:
Food Safety Modernization Act
FSMA stands for the Food Safety Modernization Act, a food handling regulation that was put into place by the Food and Drug Administration (FDA) during the U.S. Obama administration in 2011.
The FDA's Food Safety Modernization Act (FSMA) is commonly referred to as the most sweeping food safety laws reform in over 70 years. It covers topics such as how food is grown, how it is packaged, processed, shipped, and imported into the U.S.—food defense.
The ultimate goal of the FDA's Act is to make food handling safer in the United States, and to prevent food-related safety issues from sprouting up in the U.S. food supply. This includes whom you let into your production sites, and when, like visitors or contractors.
When a visitor or contractor arrives at your food manufacturing site, it’s the responsibility of your team to ensure they meet safety guidelines. At the same time, your external visitors should feel welcomed and safe.
These two outcomes shouldn't be mutually exclusive. And they don't have to be with the right visitor management system in place.
Hence, the launch of the Foreign Supplier Verification Program (FSVP) final rule that applies to most entities who import food into the United States from abroad, including domestic facilities and food brokers.
Just ask Greencore Group plc, a leading convenience food business with an annual turnover of approximately £ 1.3 billion.
Rather than just record the answers to questions on custom screens, the app enables us to act on responses with smartrules. Reception is able to engage with the visitor to get more information.
Costas Moraitis, IT Business Relationship Manager, Greencore Group plc
With constant changes being made in the way food is supplied we can always expect the threat of unforeseen food-borne illnesses—and stricter safer regulations are key to preventing them. (See our tips on streamlining health and food safety screenings)
There are 7 major areas of focus for the FSMA regulations:

What's more, a failure to comply can result in harsh punishments that range between misdemeanor convictions of $100,000 and a year of imprisonment for individual offenders, and $250,000 if a violation results in death.
For organizations, those penalties are doubled. But the cost of managing healthy safety processes across multiple sites can also add up. That's when it's good move to let your visitor management software do its job to help you maximize the visitor experience at your food manufacturing site.
Asking security-related questions, such as health information to each of our visitors entering our site, is an important aspect of our security protocol. However, managing that process across multiple sites has a significant cost.
Quentin Regout
Managing Director, Hesbaye Frost
At Proxyclick, we strive to stay on top of the changes in global regulations affecting your success in corporate governance. As such, we have prepared a host of actionable content around the topic that's updated regularly:
Browse our selection of regulatory compliance-related articles, including:
Because let's face it, nobody's going around handing out "We are compliant" badges. It simply comes down to what your company's DNA is made of.
So if you'd like to take action today, then contact us to keep this conversation going!